Secrets provide a mechanism to securely store and work with sensitive information (such as an API key) within Paperspace. Secrets can be safely injected into workloads as environment variables. An environment variable that uses a Secret does not reveal the contents of the secret itself.
When using other services that require authentication via an API key, this key can be stored as a Secret within Paperspace and then passed-into the workload that requires the API key. This would prevent the key itself from being visible to other team members. It would also guard against accidentally exposing the API key such as checking-in it into source control.
Secrets can be created at the following levels:
Team: these secrets are applied to all projects and all clusters
Project: these secrets are applied to all Workflows in a project
Cluster: these secrets are applied to all Workflows in a cluster
If the same secret name is created for more than one scope, only one is applied. Secrets with the same name have the following precedence:
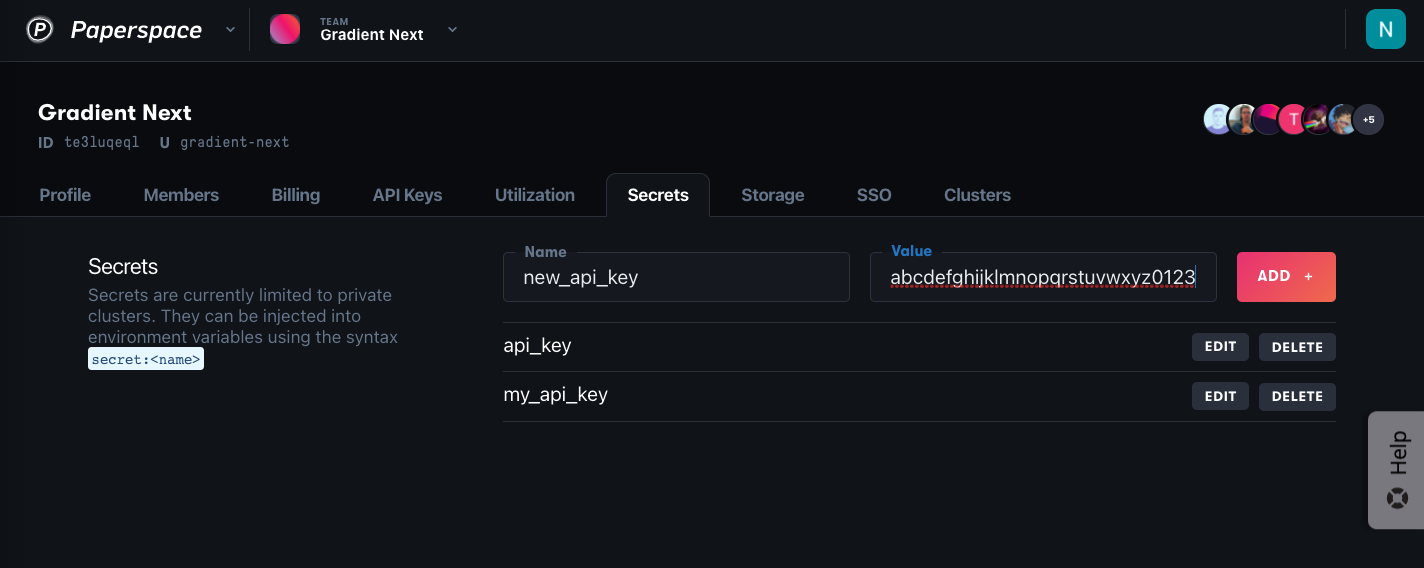
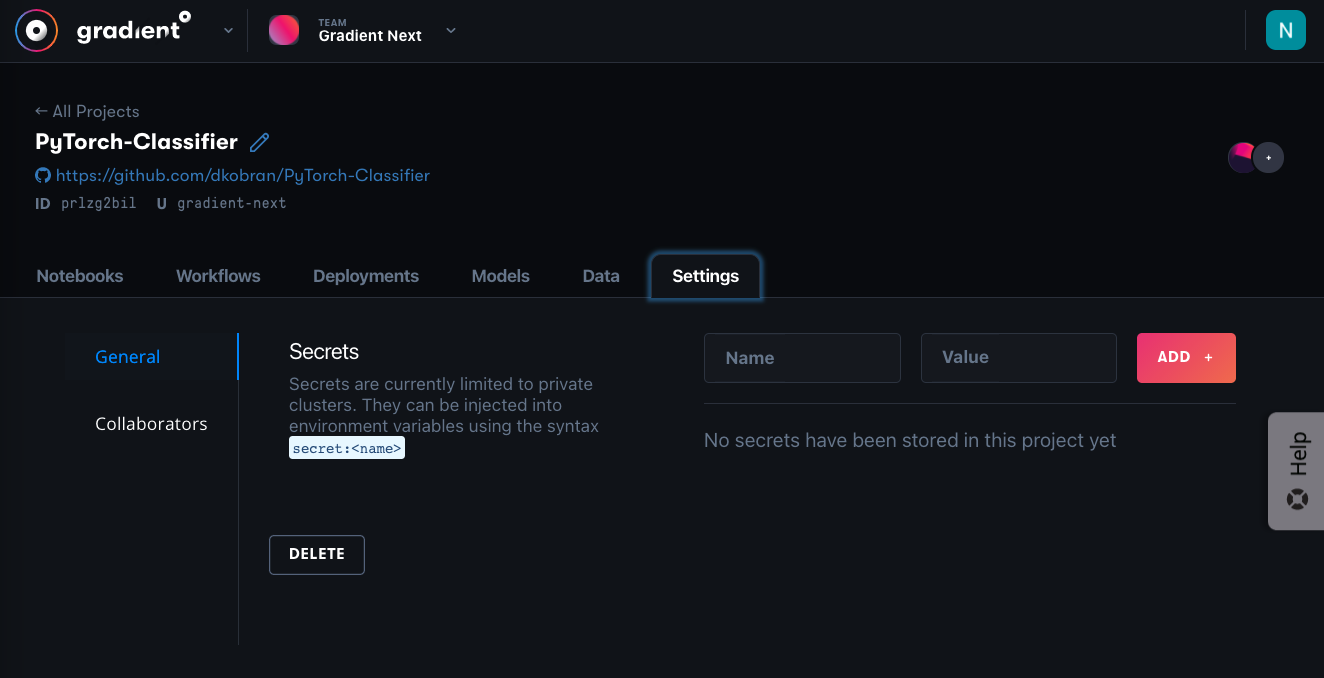
You can set secrets from the Settings tab in the console or through the CLI.
Navigate to one of the following:
The Secrets tab under Team settings
The Settings tab under a Project
The Secrets tab in the details of a Cluster under the Team settings Clusters tab
These correspond to Team, Project, and Cluster secrets respectively. Type in the name and value of the secret, and click Add to save.
Set team secret:
gradient secrets set team --name=<name> --value=<secret>
Set project secret:
gradient secrets set project --id=<project_id> --name=<name> --value=<secret>
Set cluster secret:
gradient secrets set cluster --id=<cluster_id> --name=<name> --value=<secret>
For the full list of options, see the CLI reference.
You can set secrets from the Settings tab in the console or through the CLI.
Navigate to the Project, Team, or Cluster page, as with setting a secret above. The names of secrets in that scope that are already stored are listed.
List team secrets:
gradient secrets list team
List project secrets:
gradient secrets list project --id=<Project ID>
List cluster secrets:
gradient secrets list cluster --id=<Cluster ID>
Navigate to the Project, Team, or Cluster page, as with setting a secret above. Click the Delete button and confirm the dialog.
Delete team secret:
gradient secrets delete team --name=<name>
Delete project secret:
gradient secrets delete project --id=<Project ID> --name=<name>
Delete cluster secrets:
gradient secrets delete cluster --id=<Cluster ID> --name=<name>
Certain actions within Gradient require incorporating your API key to authenticate requests. In cases where your API key is used within your code or commands that may be visible within your Gradient team (for example, a Notebook) or other locations (for example when checking your code into source control), you can use Secrets to mask your unique API key.
Create a new API key.
Go to the API Keys tab under team settings, type a name for the key, and click Add.
Once your key is created, copy the key to your clipboard.
Save the key as a Secret.
API keys can be added in a similar way to other secrets: type a name, paste the API key in the Value field, and click Add.